Building a more secure remote access setup with Tailscale to access Vaultwarden and Synology remotely
About two months ago, I deployed Tailscale to provide a secure remote access solution to my internal (home) network. If you’re not familiar with Tailscale, please check out my previous article on the basic setup. As a quick primer on Tailscale security, check their docs here.
Since then, I’ve built a more secure solution with Tailscale, specifically to allow me to access my internal services more efficiently and securely. This post will describe this setup and configuration.
The big picture
A picture tells more than a thousand tweets, so here’s the solution:
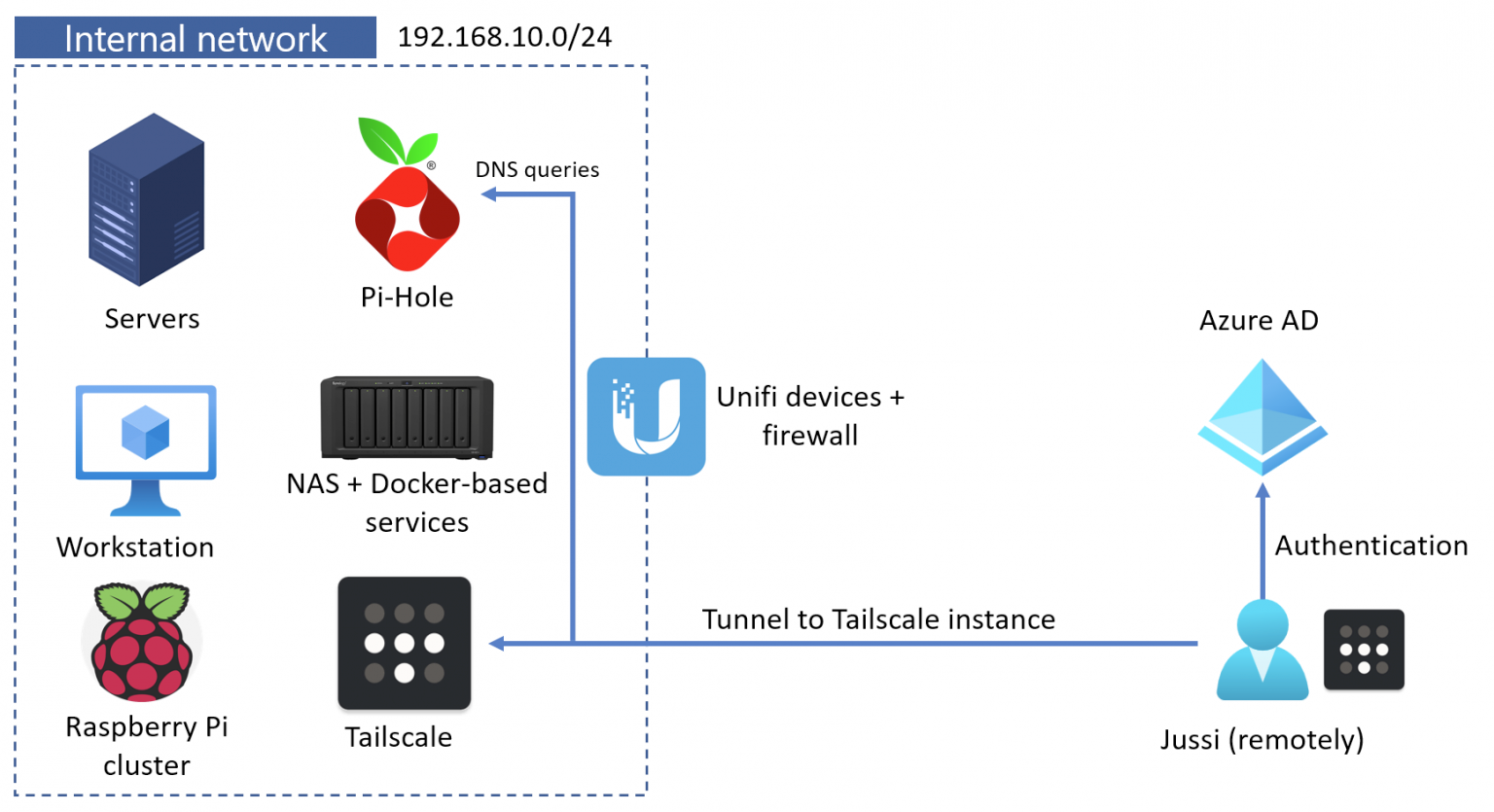
This setup allows me to remove all publishing rules on my firewall. I no longer need to open ports or use NAT to grant me access to my internal Synology NAS, my Vaultwarden password management tool, my Raspberry Pi cluster, or anything else I need to access remotely when not at home. I could also remove the QuickConnect feature from my Synology device.
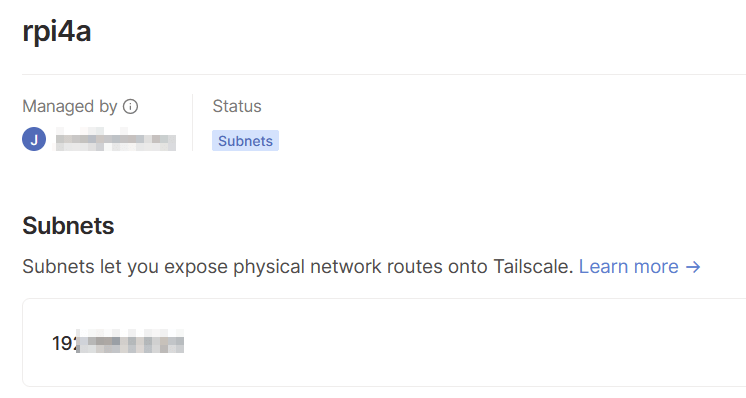
I have a secure VPN tunnel to my internal network using my laptop (and other devices I have on me when traveling). I have one Raspberry Pi configured to expose my internal IPv4 subnet for my Tailscale tunnel. It’s a feature that allows me to ping any internal IP when connecting to the Tailscale subnet.
So, when my laptop connects with mobile data when I’m not at home, it gets a Tailscale IP of 100.15.10.5. It can then connect to any device connected to my internal network of 192.168.10.0/24. I can also directly connect to other Tailscale-enabled devices within the Tailscale subnet. Through this, I have access to all of my internal services and devices without needing to punch holes in my firewall.
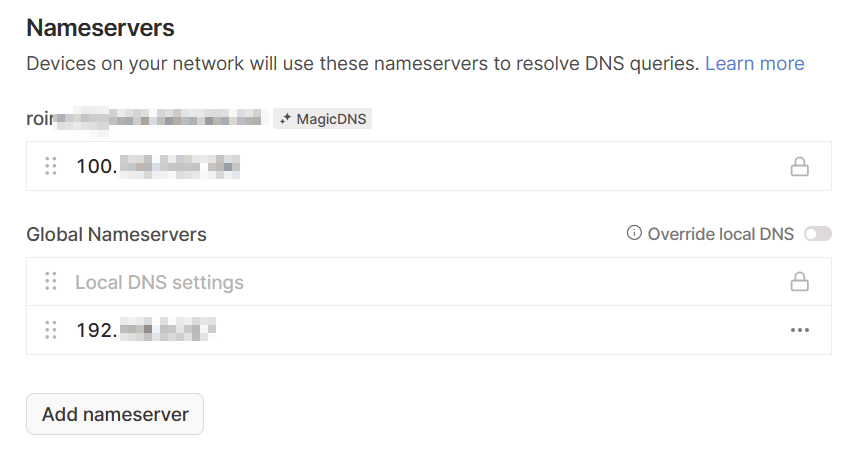
Lastly, I’m utilizing the Magic DNS capability of Tailscale to lookup DNS entries from my internal DNS service – a Pi-Hole instance. I’ve added Pi-Hole as a global nameserver. Within Pi-Hole, I’ve added local entries for my core services.
With this setup, any of my devices can reach any of my other devices regardless of where these devices are. And everything feels as if they’re directly connected in the same LAN. At the same time, I am utilizing Tailscale’s VPN tunneling (based on WireGuard).
A nice but necessary bonus is that Tailscale uses one of my Microsoft 365 identities for authentication. And that account is fully passwordless.
Why is it more secure than previously?
With the recent Log4j vulnerability, I started checking my home firewall settings. I didn’t have too many open rules, but several open endpoints were necessary: my password management tool, the Synology NAS, and a few other services. I wanted to close all of these ports and publishing rules, which led me to dive deeper into how Tailscale could add more security.
Now I can access the following services via the secure tunnel:
- SSH endpoints on all of my devices
- RDP endpoints on all of my devices
- The Synology NAS admin interface
- PiHole (for DNS queries globally)
- File shares
- Backup systems
- Printers
- Wi-Fi and other network infrastructure services such as DHCP management
- Philips Hue
As each device that hops into the Tailscale network requires my Azure AD-based identity, I’m glad I can secure my network end-to-end using a secure account. I can also close the Tailscale tunnel quickly on a device where I don’t need it at a given time, which effectively ensures nothing can access my internal network from the device.