Managing cybersecurity risks and vulnerabilities with Microsoft Security Exposure Management

Back in 2013 or so, I spent much of my time advocating and implementing multi-factor authentication for my customers. It felt like the pinnacle of security: a strong password and an additional factor to ensure it's you, perhaps something as modern as a PIN code via a text message.
Much has changed since then, not the fact that you need phishing-resistant authentication capabilities, that everything should be encrypted, or that you really shouldn't trust anyone or anything, and aim for Zero Trust.
A traditional approach to managing cybersecurity risks and vulnerabilities in the cloud (and on-premises) has been refreshed among all these considerations. This is called Microsoft Security Exposure Management, or MSEM for short. It's been under the radar, so I wanted to provide insights and share my experiences deploying it.
Overview of Microsoft Security Exposure Management
MSEM is a cloud-based set of features, bundled under the Microsoft Defender XDR set of services. You can access MSEM via https://security.microsoft.com, and you'd typically use, view, configure, and analyze data in MSEM as a security analyst, operator, or administrator.
On the surface, it doesn't look like much. What's important to understand is that MSEM is pulling together many security reports, initiatives, and views from other services, thus allowing you to see your environment's security exposure and vulnerabilities centrally. It aims to answer a single question: "How protected is my organization?"
An overview of your organization presents a 360° view of your organization's critical assets, possible attack paths, initiatives, and how well you're protecting your assets.
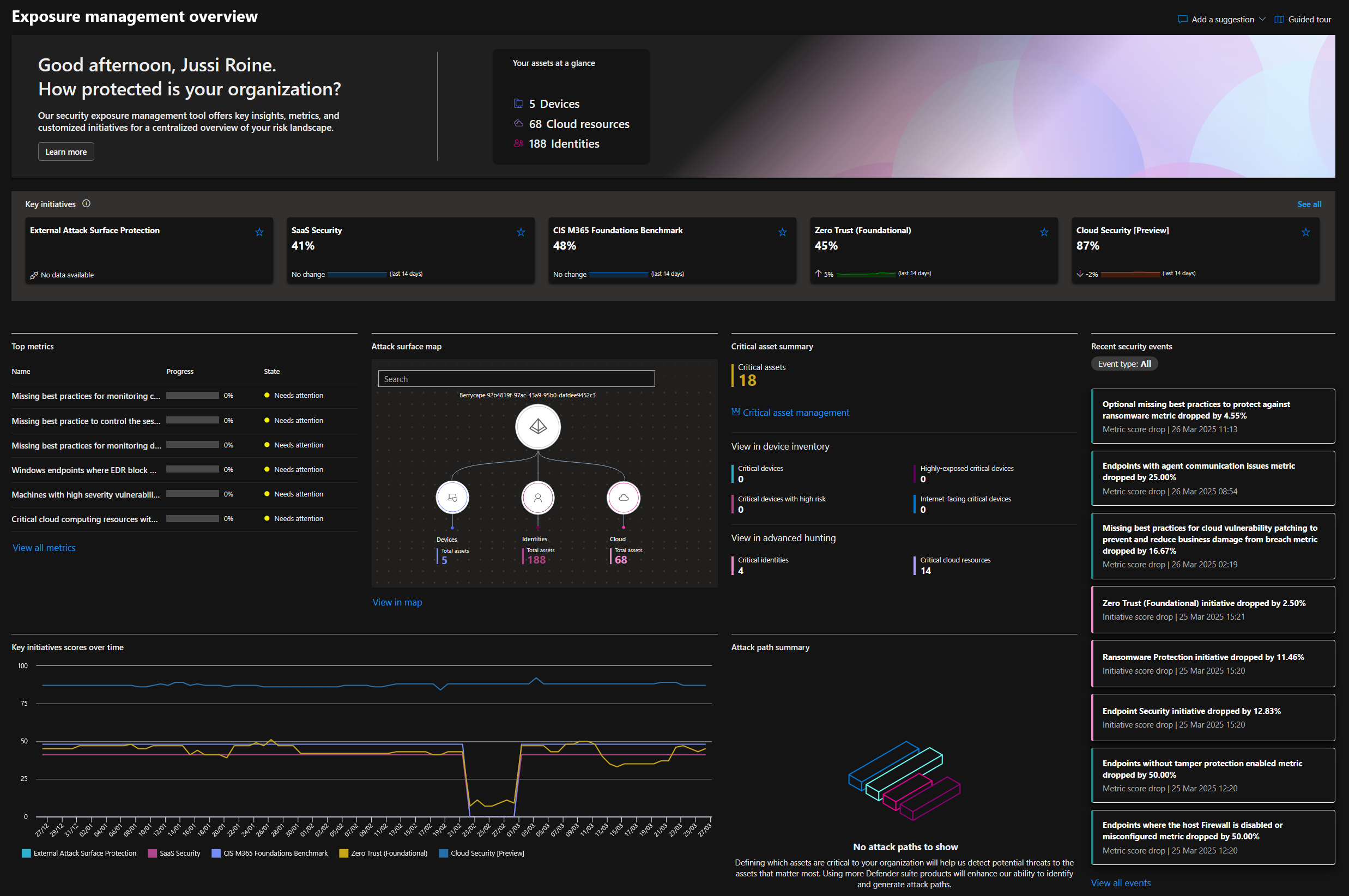
We can see a snapshot of the key initiatives, such as Zero Trust, business email security, and cloud security. We also get a list of the distribution of our critical assets, such as user devices, servers, and identities.
Many capabilities here will lead you to other Defender XDR and Azure security capabilities. In contrast, others allow you to drill deeper and will pull relevant data and recommendations from those services. Prepare to have a lot of tabs open when working with MSEM.
Understanding exposure initiatives and attack surface
Beyond the overview, the capabilities in MSEM revolve around exposure initiatives and attack surface management.
Exposure initiatives include pre-defined initiatives for all significant cybersecurity aspects, such as
- Business email compromise
- CIS Microsoft 365 Foundations benchmark
- Cloud Security
- Critical Asset Protection
- Endpoint security
- Ransomware protection
- Zero Trust
- Vulnerability assessment
Each initiative pulls together the current state of said capabilities, recommendations, critical actions, mitigations, and relevant security metrics. Business email compromise, for example, looks like this:
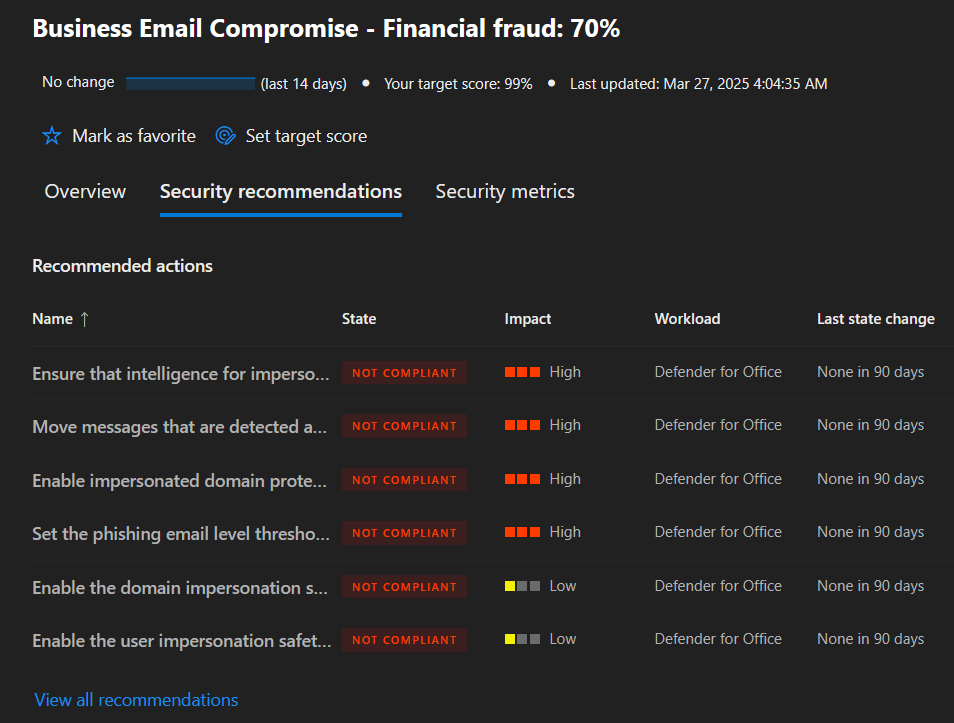
I can see that I am at 70% completion, and I need to work on high-impact actions to ensure better business email security. I've set the target for all initiatives to 99%. As expected, Defender for Office is utilized to pull these stats for me - I could go to that specific capability to review the same data. Still, MSEM is bringing all of these together for me, making it much easier to understand what's happening across the organization.
Selecting a security recommendation allows me to examine what configuration is needed and how it relates to the overall system.
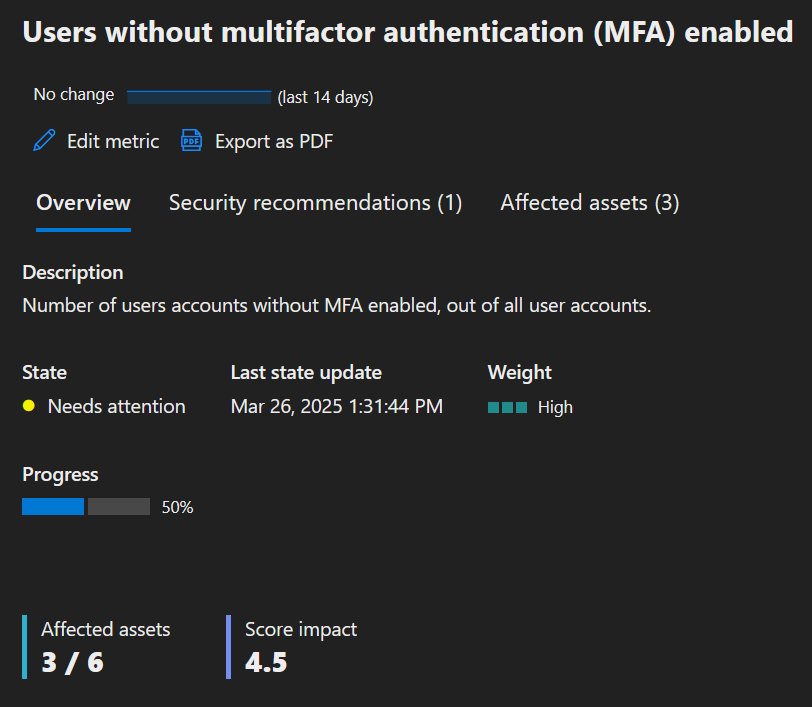
This makes it much more straightforward to craft reports and summaries and to work on high-impact security recommendations in a single view. As is often the case, security controls require cross-organization collaboration from relevant SMEs; allowing me to work on these rapidly will make tackling them easier within initiatives.
A detailed changelog is also provided to track what has changed over time.
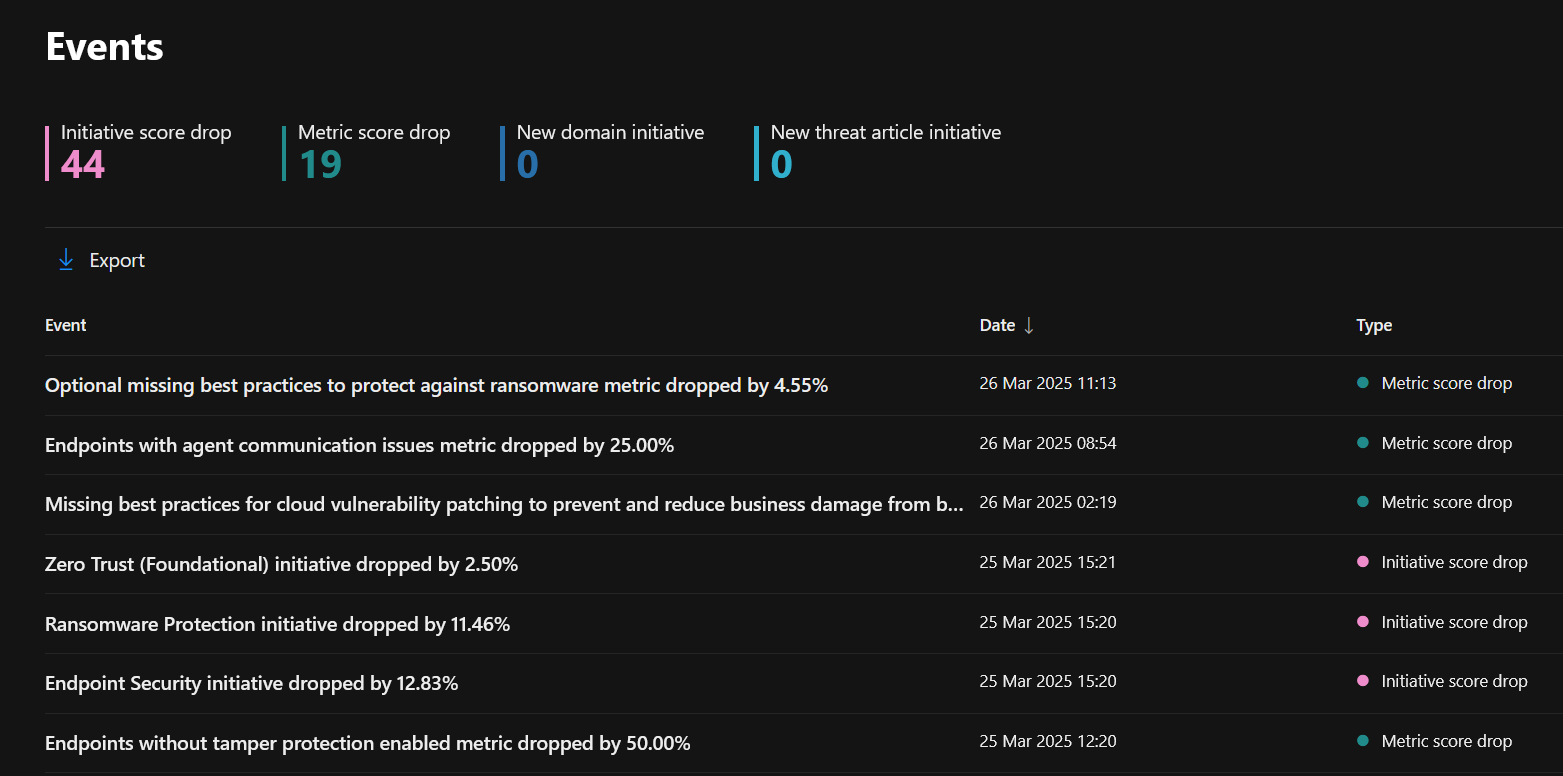
Initiatives are the bread and butter of MSEM—they pull together pre-defined constructs that aid in bettering the security stance of a given business capability, such as email or endpoints.
I recommend starting with a single initiative to get the hang of it, and treat the recommendations as they are.
Attack surface
While initiatives above are for proactively working on possible security issues and ensuring your organization is protected in the best possible way, Attack Surface allows you to hunt, and drill down deeper into finding current issues and risks.
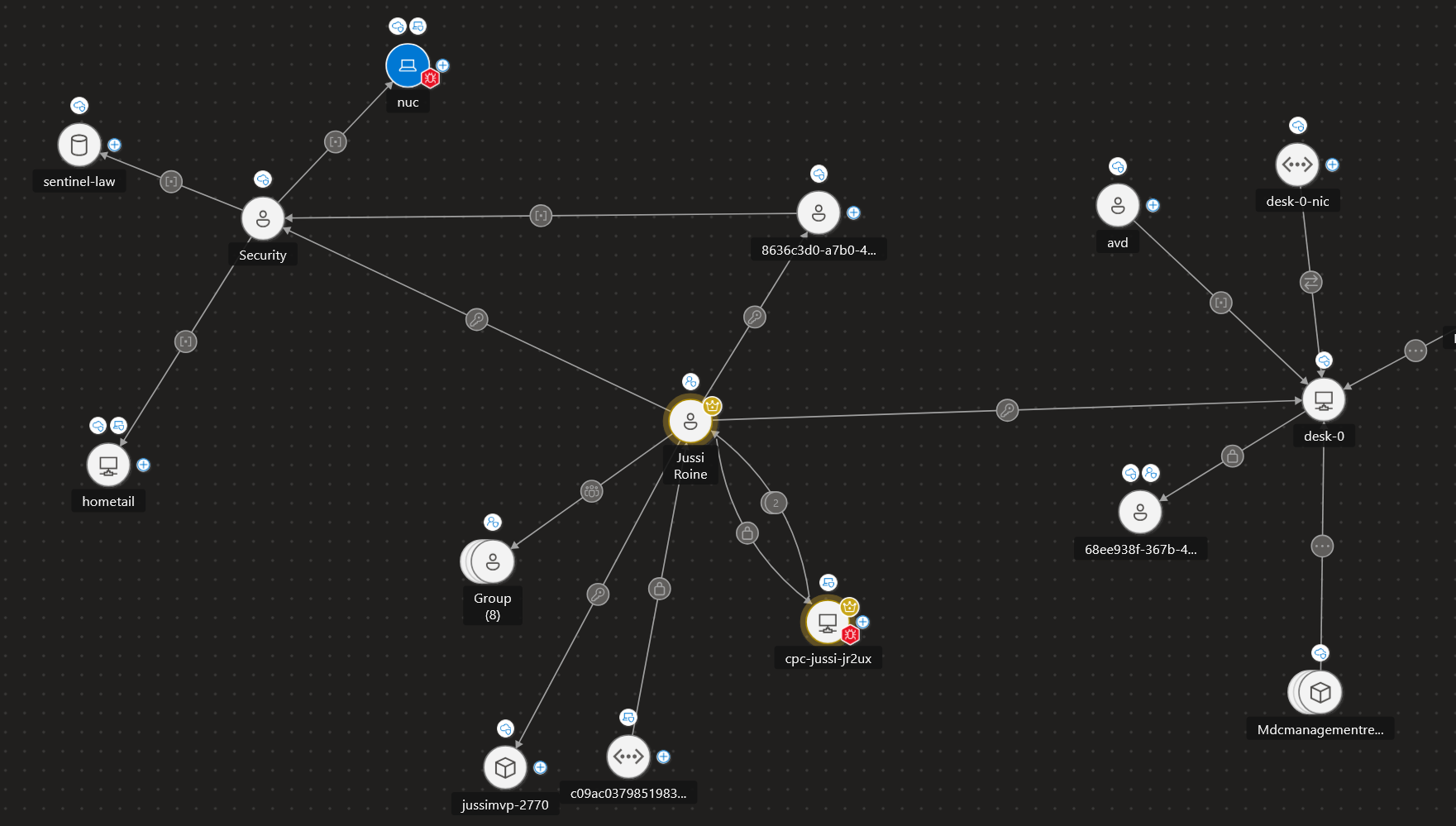
Attack surface provides a map of all of your assets. Some assets are automatically added to the inventory and processed, while others you might want to add manually. This includes on-premises servers and services, multi-cloud services, identities, endpoints (meaning workstations and laptops that are onboarded to Defender for Endpoint), as well as Azure assets such as virtual machines, databases and workloads.
By visualizing the landscape, it becomes easier to spot issues. In the image above, you can see one of my virtual machines - which is a VDI instance in Azure - has vulnerabilities. Drilling down straight from the map provides me with tangible advice:

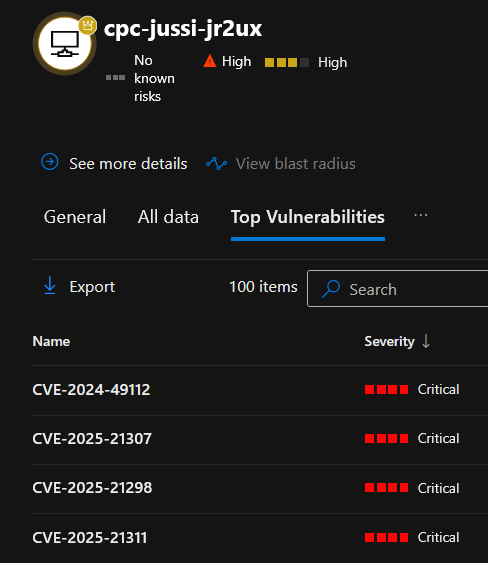
Once you drill down further from this view, you'll end up in Defender for Endpoint's device features. This is the power of MSEM - without needing to go to multiple portals, you get direct advice and a shortcut to those tasks.
In closing
Microsoft Security Exposure Management is a much needed and welcomed service. I've barely scratched the surface in this post, as I feel not many people realize the power of initiatives and attack surfaces. It extends from here to additional capabilities, such as those that Defender for Cloud from Azure provides.
Have a look at MSEM, and start protecting your organization today!
Additional reading
Reach out if I can help
I work as a Senior Security Architect at a company I co-founded, Not Bad Security. Feel free to reach out to me, if I can assist you with any Microsoft security related deployments, assessments or troubleshooting.