A practical look at using Cloudflare to protect and optimize my site

About a month ago, I decided to remove all Google Analytics tracking, telemetry, and analytics from this site. Initially, I started using GA years ago, when I wanted to see what kind of content seems interesting for my audience, and – over time – the content is being accessed. It was beneficial to know and still is.
However, I began to worry about the cookies Google injects as part of their tracking script. I then had a look at the number of cookies my site has: One cookie for the Twitter button on the sidebar, two for Google Analytics, and one more for my newsletter signup (via Mailchimp). Once I removed all Google-related scripts and converted the Twitter button to a static image, I am down to just one cookie: the Mailchimp cookie for signing up for my newsletter. I think that’s fair and very reasonable for my audience.
Cloudflare is a company providing all sorts of interesting services. Recently, their Web Analytics solution hit my radar, and I enrolled for the free tier. It’s very bare-bones, but in a good way: no customer segmentation, funnels, and all sorts of extraction schemes—just anonymized data on what sort of traffic my site is receiving.
Here is the Cloudflare Web Analytics main interface:
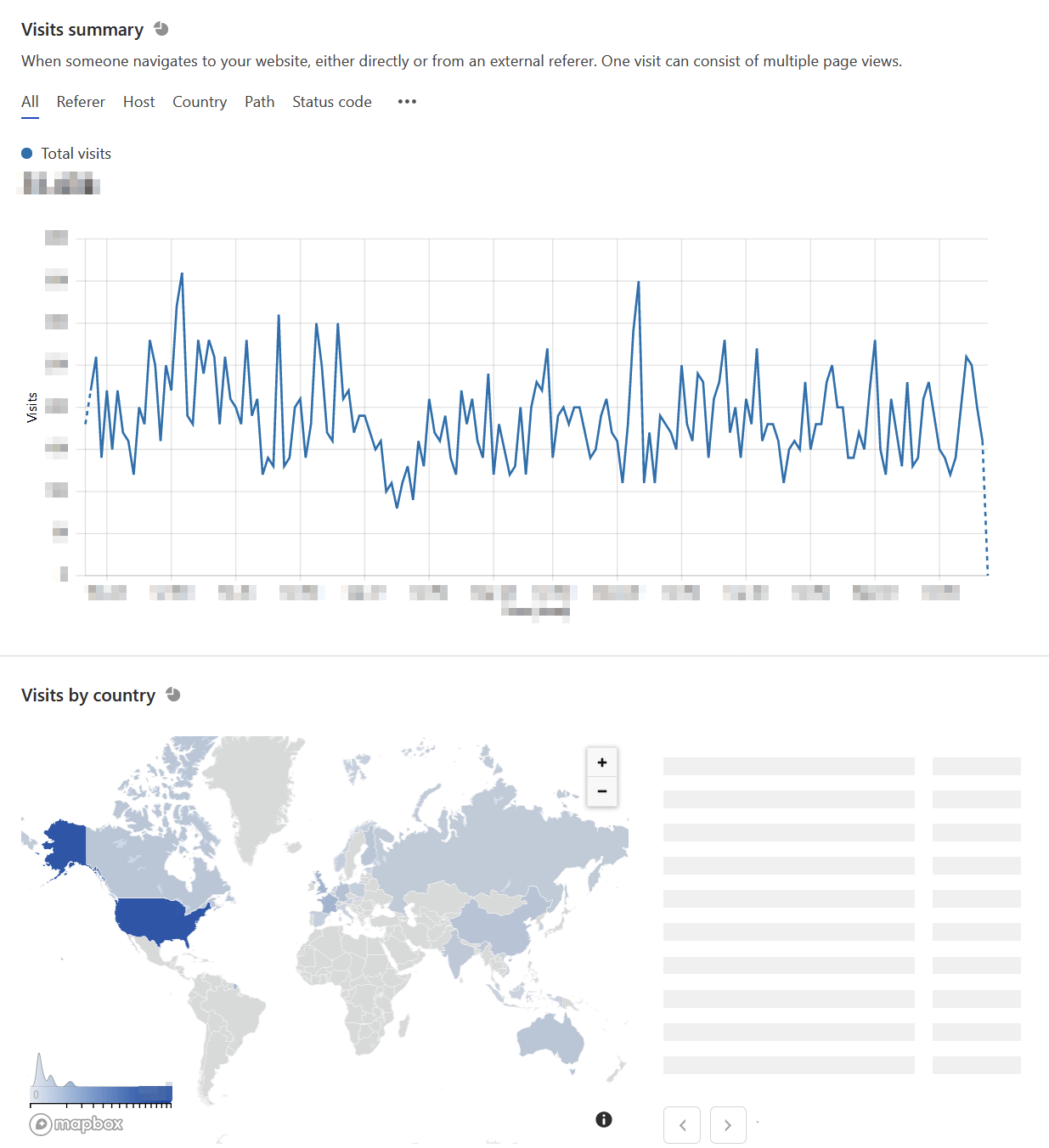
It also reveals which content was most visited during a selected time period, and what device types were used.
I love the simplicity so much that I don’t really need to see the charts and statistics too often. Perhaps once a week, I take a peek, and it’s reassuring to know that there is traffic.
The base license is free, and it includes a bunch of other services: a global Content Delivery Network (CDN), mitigation for DDoS attacks, and such. Once I had signed up, I began to look around – what else is available?
The toolbar within the Cloudflare portal shows a lot of features:
I’m utilizing almost everything here, but not to the full extent they offer. A quick run-down of the services that I use for this site:
Analytics: Website visitors (#), data transfer amount, # of requests, possible threats identified, website performance.
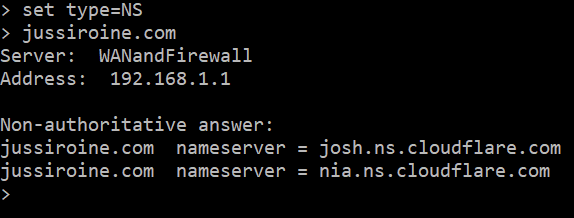
DNS: In order to get Cloudflare work for you, DNS has to relocated for their platform:
Spectrum: I have no idea what this does, but I think it allows you to protect specific applications. The current list of apps lists just SSH and Minecraft.
SSL/TLS: I’m using end-to-end encryption, meaning that browsers connect to the Cloudflare edge services, and Cloudflare passes that traffic to my service. Everything is over SSL/TLS. A lot of configurability here, such as edge certificates, HSTS support, always enforce HTTPS, and similar. I flipped most settings to On.
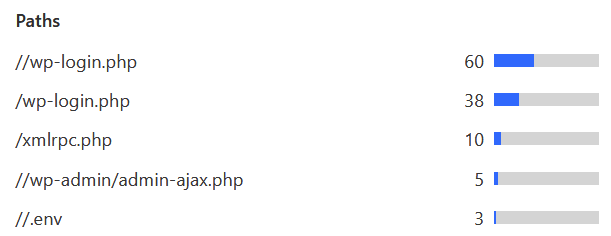
Firewall: Here is where it gets super interesting. I utilize the Cloudflare Firewall for weeding out obvious scanning and hacking attempts. For the past 24 hours, I see HTTP requests to:
I’ve configured the firewall to enforce a JavaScript-based challenge when such an attempt occurs. This usually helps in avoiding automatic scanning bots and scripts. For the same past 24 hours, I am seeing this JS challenge being enforced almost every hour of the day:
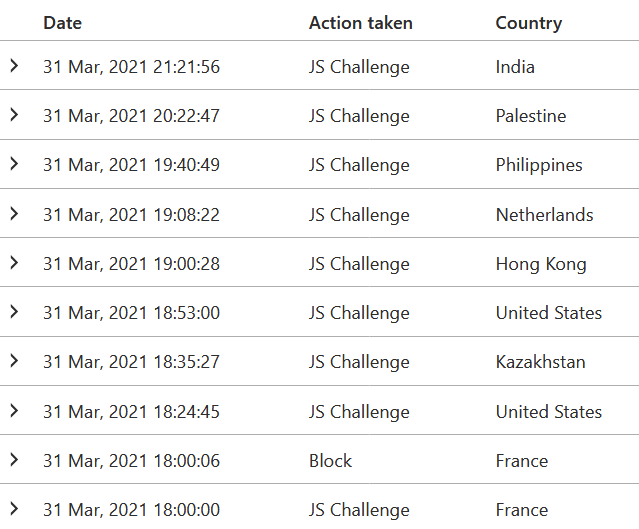
The firewall also has built-in rules that I’m utilized. The custom rules I have, include fairly simple – yet powerful – restrictions. Out of all traffic that seems suspicious, only 1.7 % resolved the JS challenge. The rest failed, so I assume they gave up and moved on. One of the custom rules checks for any HTTP requests to /wp-login.php, for example. The built-in analytics for the firewall also reveals that 85% of said traffic is a verified bot (which doesn’t inherently means it’s hostile, just that it’s a bot trying to scan or request something):
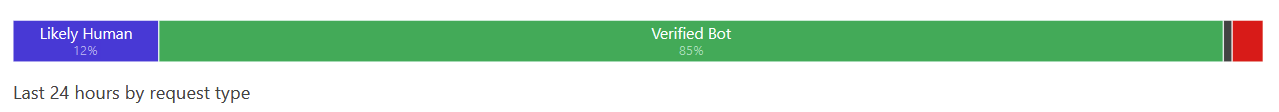
(the small red portion is for ‘likely automated’ traffic)
Speed: I’m utilizing some Cloudflare optimizations, thanks to their CDN, to speed up page load times. For the first few weeks, content is being painted to browsers globally 25% faster.
Cache: I utilize aggressive caching, as my content is either freshly updated or remains the same once published. About 84% of all content hits the cache now. I’ve set the Time-To-Live for cache to 8 hours.
Traffic: A service called Argo lives here, and it aims to deliver responses to users more quickly. This is one of the few services that have an additional cost based on the amount of data served.
There are numerous other – perhaps tiny – settings I’ve enabled, but the core services and settings I utilize from Cloudflare are these.
To get all this working, a plugin in WordPress is installed, called Cloudflare. It was recommended to perform configuration from Cloudflare’s services and ensure cache settings are optimally set.
How much does all of this cost, then? I’ve now had these running for about a month. The invoice is based on the following components:
- Cloudflare Pro Plan: $20/month
- Argo traffic: $5
- Total: $25/month
Perhaps the primary value I seem to be getting is caching and a firewall. I frequently now see about 10-20% speed improvements globally – more for regions closer to me and slightly less for regions further away. Obviously, web analytics is a key thing I utilize, but that was already free, to begin with.
I also appreciate that Cloudflare is very authentic. If you don’t like the service, there is no lock-in for me as a customer. I can simply reconfigure my DNS, and wave goodbye to the service and stop paying for it.