Thoughts on the Garmin outage and possible ransomware attack

Last week, Garmin’s services mostly went down. This meant that all Garmin devices, among others, wouldn’t sync data between the mobile app (Garmin Connect) and Garmin’s cloud-based services. You also couldn’t configure a new Garmin watch, for example.
Garmin was very tight-lipped about the incident. On July 23, about 20 hours after the incident began, Garmin updated these two tweets on Twitter:
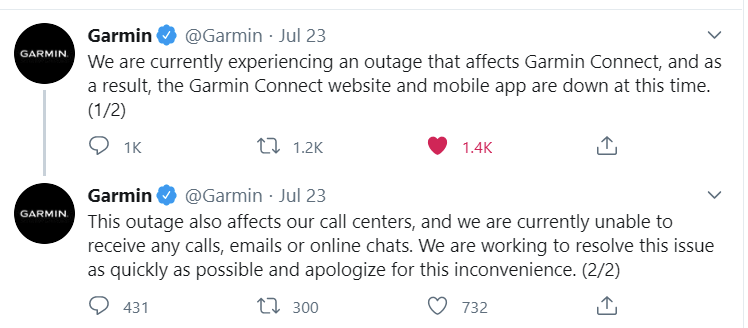
At the time, they called it an outage. I took interest in the wording of the second tweet – an IT outage of production-grade services does not usually put out call centers, email services, and online chats. Especially for an established company that has an annual revenue of more than 3 billion dollars. Usually, this might mean it’s a panic move to shut down everything to investigate and assess.
People on discussion forums and chats were furious, even livid. My own experience was relatively unaffected. The Garmin Fenix 6X Pro that I use daily continued working normally. I couldn’t synchronize anything to the cloud to analyze anything, but most data I could view on the watch directly. As the watch stores everything in local storage, I didn’t have a reason to panic about my statistics or data I’m accumulating. I went to the gym normally and did a few runs – all good.
In all years I’ve relied on Garmin devices, their services have never been down for me. They are rock solid. It partially offsets the premium price of the devices for me.
Over the weekend I trawled through the news to see if Garmin announced anything related to the outage. Quite soon after the incident, BleepingComputer published a piece that seemed to confirm the outage was the result of a hostile ransomware attack, called WastedLocker. That was worrying for several reasons.
First, if it truly was a ransomware attack – and a sophisticated one at that – it would mean that Garmin scrambled to get anything up and running. I would imagine that losing data was the last alternative for them. Perhaps if the ransomware had been successful enough to infiltrate through mounted backup storage, or even offline tapes (through months of silently encrypting data behind the scenes), it would be a drastic blow to Garmin’s recovery effects.
Second, if Garmin had proper backups, I imagined they would bring in third-party experts to assess the situation – airgap everything, start building a fresh infrastructure while analyzing the infected networks and data, and try to break the encryption.
And third, Garmin was very silent about the whole incident. First, it was an outage. Then a few days later, on July 27, BleepingComputer published another piece with evidence of the ransomware attack. The services started slowly turn green again and resume their operations early this week.
Ars Technica also published an article on the situation, with references to this Sky News article, claiming that Garmin acquired the decryption key. The wording that someone (anonymously) close to the situation gave, was that Garmin did not directly make the payment to the hackers.
It would explain how the services ‘suddenly’ resumed as if they’d just been turned back on early this week. Once you put in the decryption key, you should have access to your data again. I’m not a forensics or security expert, and I’m sure Garmin will spend months cleaning up after this.
EY has a great flowchart on the payment decision process here. In all simplicity, one either evaluates the recovery options and/or starts to negotiate the ransom payment.
If they ended up paying (through an intermediary), it certainly tarnishes the brand and image of Garmin for many. Myself included. Admittedly, if the ransom was – as alleged – $10 million, it’s equivalent to what Garmin spends annually on the free snacks at their offices. It’s certainly frustrating to think, that poor or mediocre handling of their IT systems resulted in consumers like myself – possibly – in the future paying a portion of their ransomware fees.
I wouldn’t know what I would do in a situation like that. Perhaps weighing between paying $10 million now and moving forward, or spending weeks – or months – rebuilding everything was an obvious decision to make.
I trust and hope that Garmin manages to resume all services, and invests more in the future to avoid this happening again. I doubt we’ll get a post-mortem of the situation, as there would be no upside for Garmin (or their insurers) to reveal much beyond what they’ve already stated.
[ Edit August 4, 2020: BleepingComputer seems to confirm that Garmin did, indeed, pay for the decryptor through an intermediary company called Arete IR. ]