Building a site-to-site VPN between Unifi network hardware and Azure

At home, I run Ubiquity Networks’ Unifi hardware. I wrote briefly about this just recently here, and I also found out the Unifi hardware provides a neat way to generate a network topology map, such as this:
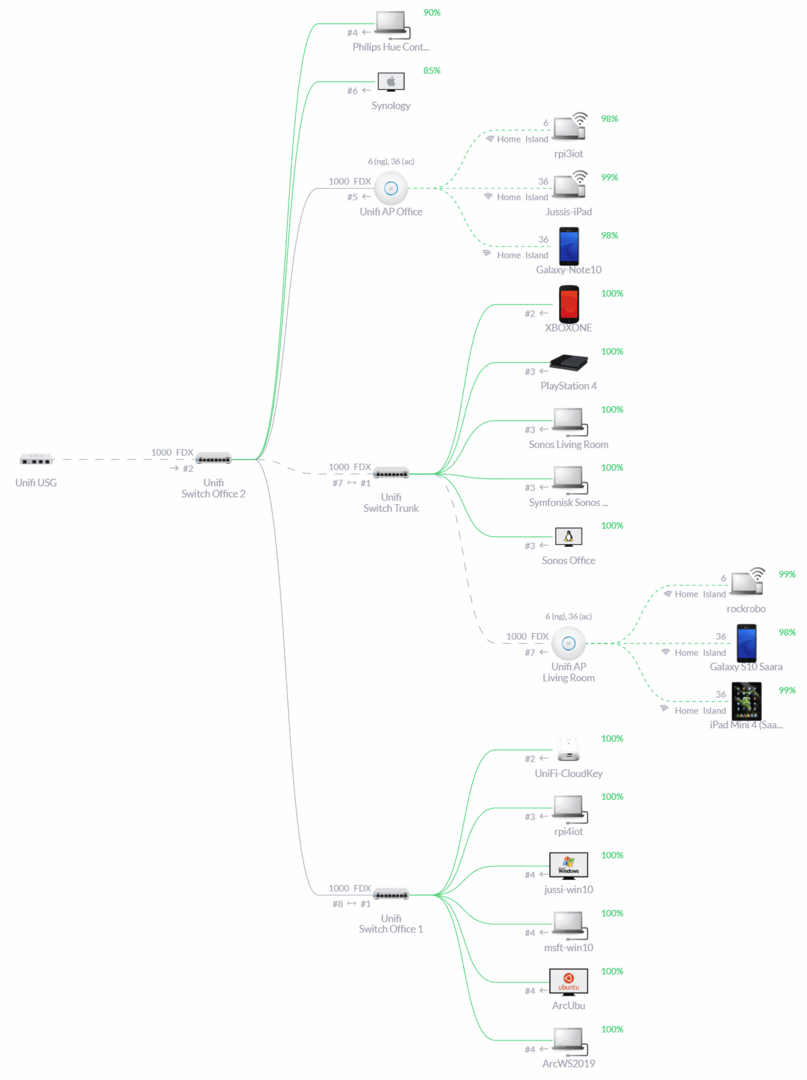
In essence, I have the Unifi USG as a firewall, and 3 Unifi 8-port switches around the house to provide connectivity for my wired and wireless devices. The Unifi 8-port switches are managed 1 Gbit switches – very reliable, and quite affordable also. The whole thing is managed via Unifi’s Cloud Key – a small huppeldepup, providing remote management capabilities. You could also run it in a VM, or a Docker container, but the warm feeling of having a solid hardware device is something else.
So, as I have this infrastructure up and running, I wanted to build a site-to-site VPN between my site (home) and Azure. It isn’t a huge task, as S2S VPN’s have been around for a long time by now, and Azure has supported this model of connectivity for years.
Building the Azure side
This is well documented, and I didn’t encounter any issues. In essence, you’ll need to:
- Create a virtual network (VNET) in Azure with the desired address space. I used 10.1.0.0/16 for the network
- Create the VPN Gateway – this is the Azure-side, and it requires a separate subnet from the virtual network called GatewaySubnet – and that has its own C-class address range of 10.1.1.0/24. When provisioning the VPN Gateway you can define the VPN Type and SKU. The VPN Type has to be Route-based, and the SKU is dependent on what bandwidth and capabilities you require. For me, I chose the cheapest SKU called Basic. You can review the capabilities and pricing here. The Basic gives me 100 Mbps bandwidth and up to 10 S2S tunnels, costing me about 22 € (~$25) a month.
- Create a local network gateway. This identifies your local (on-premises) network gateway, so for this, you’ll need the public IP of your local network. I’m still using the Raspberry Pi-based IoT-solution to define this, see details here.
And that’s all there is. You can click-and-configure these through the Azure Portal, or use command-line tools to provision them. I like to use the Portal, as usually, I need to do these types of configurations only once.
Building the Unifi side
Configuring the S2S VPN on the Unifi side is also relatively easy, although it took a few retries to get this right. Unifi devices can be managed through its own portal. or directly through an SSH session. I chose to use the portal, as it’s the usually recommended way when working with Unifi.
First, under Settings > Networks, create a new VPN connection.
Select Manual IPSec as the VPN Type. Enable it for Site-to-Site VPN.
For the remote subnets, define the subnet you have in Azure – 10.1.0.0/24.
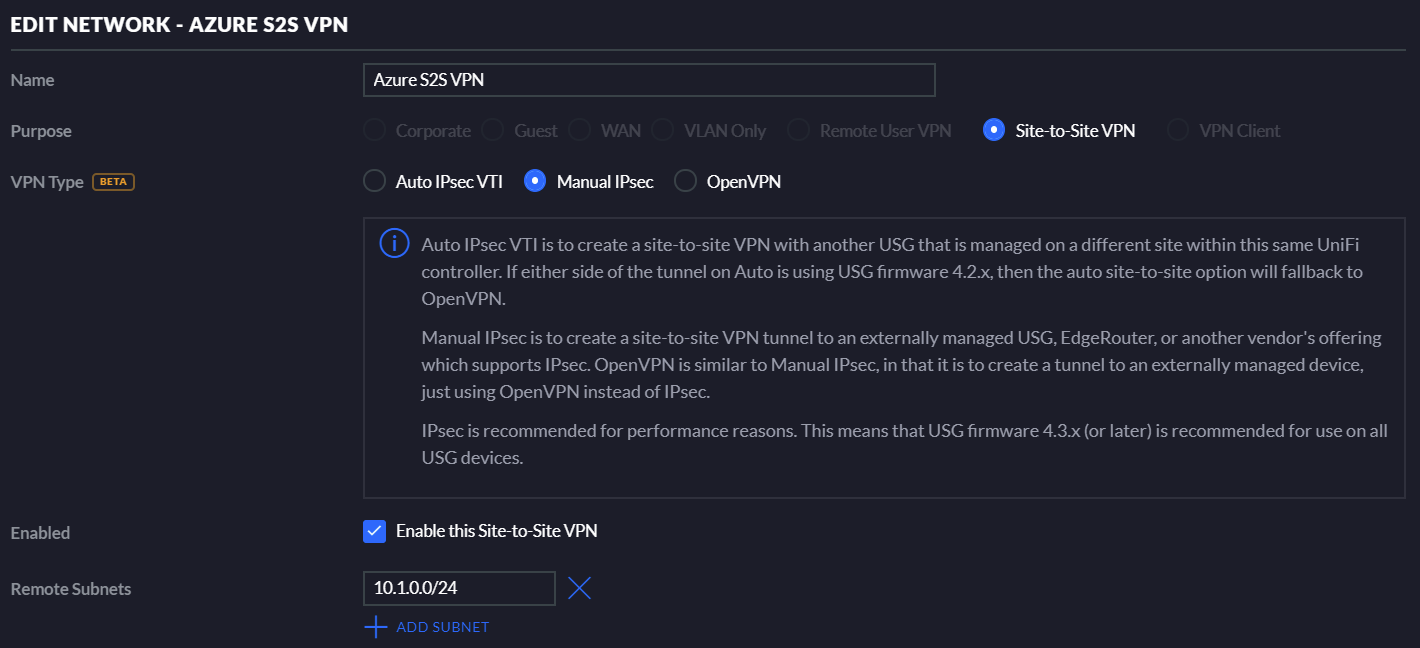
Define the Peer IP (Azure VPN Gateway’s IP address), Local WAN IP (your public IP) and the pre-shared key you defined on the Azure side.
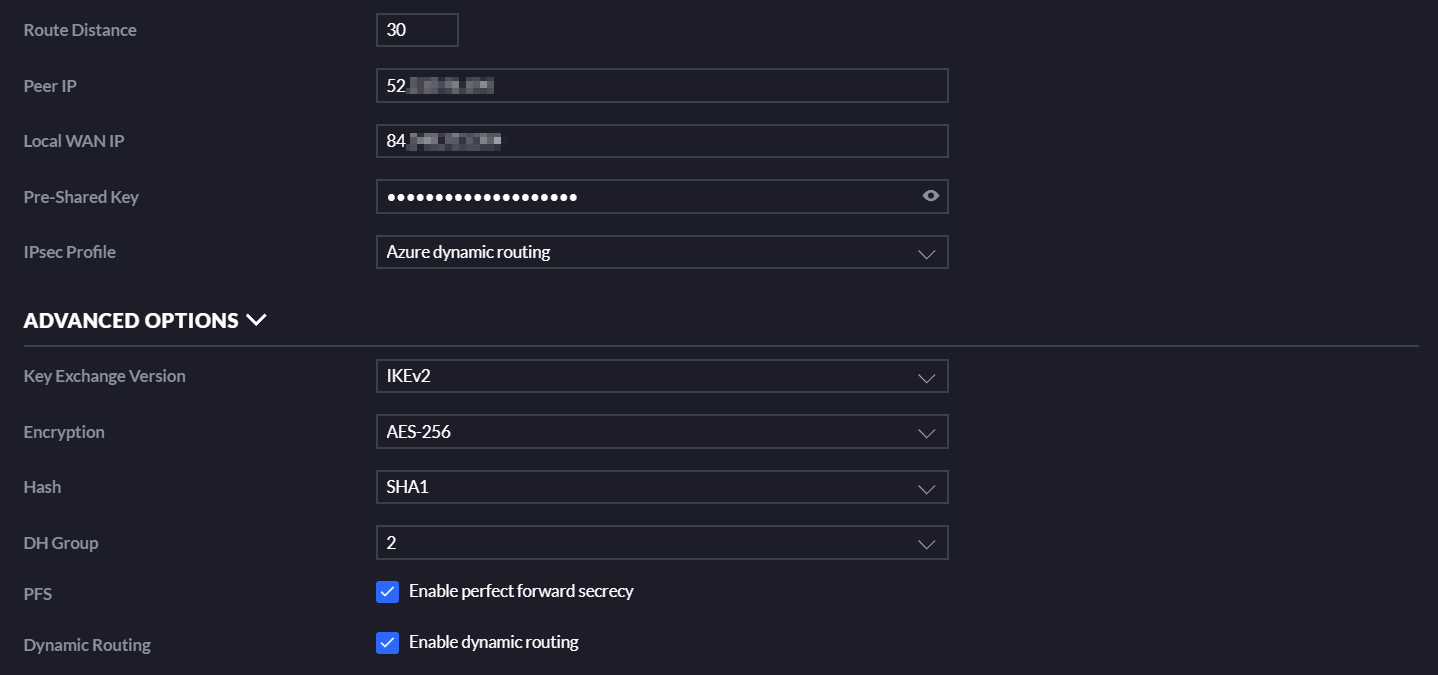
Then, the fun thing – Unifi apparently has a bug in the UI, where PFS and Dynamic Routing are always checked, even if you uncheck them. So, uncheck them! And don’t look back.
Testing the connection
That wasn’t too bad, was it? So, time to test it! Navigate to your Azure Virtual Network Gateway and click Connections.
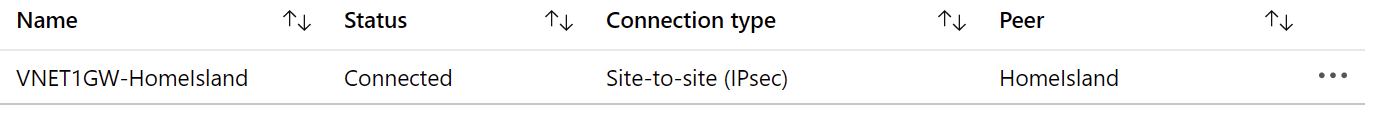
Status should update to Connected after a few minutes. I’ve noticed with Unifi that certain changes might sometimes take up to 5 minutes to apply.
You can use the VPN Troubleshoot tool under each connection to try and track any possible issues.
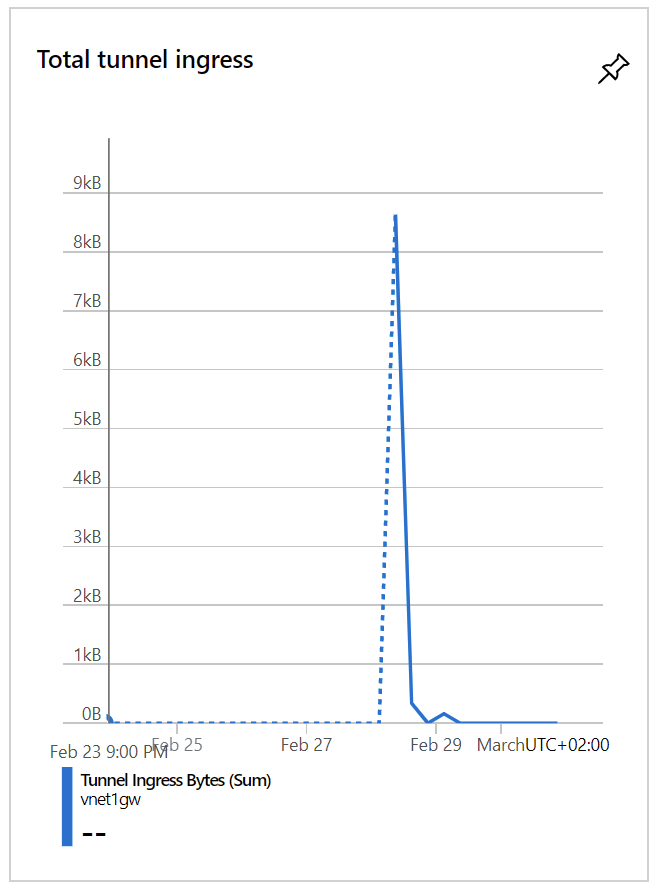
And when you push a bit of traffic through the VPN, it reflects almost immediately in the metrics for the Virtual Network Gateway:
You might notice I didn’t configure much else on the Unifi side. As this is for demo purposes, I didn’t immediately start configuring access-lists, routing rules or other crucial things. Time to do those later!