Becoming passwordless in Microsoft 365 using Surface Go and a FIDO2 key

I purchased a Surface Go device in the summer of 2018 while I was visiting New York City. It was also the same weekend when Surface Go was made available, so I opted for the 8 GB/128 GB model, without LTE. I figured I would use the device on the road, and when writing in coffee shops.
Almost a year later, I find I haven’t had too much use for the device. In my daily routines, I use my workstation PC at home and my Lenovo laptop when on the road. I rarely, if ever, take the Surface Go with me, even if it now shares the same charging capability via USB-C with my Lenovo Thinkpad. It’s a little bit too sluggish for serious work, and it’s a little bit too cramped to type comfortably. This is perhaps the reason also why I don’t own an iPad with a keyboard.
I’ve kept the Surface Go up-to-date, and it runs Windows 10 Pro with the latest stable 1903 bits (May 2019 Update). I’ve logged in with a local account, as I do not need to share anything beyond what I can synchronize with Dropbox, my go-to productivity tool when working with multiple machines. I also use Synology devices extensively for this purpose.
Last week, the Azure Active Directory Identity team announced that passwordless capabilities are now in public preview with support for FIDO2 security keys for anyone to try out.
FIDO2 security keys are industry-standard devices (usually USB sticks or NFC-enabled devices), and there are several vendors such as Yubico and Feitian Technologies. I’d purchased a few FIDO2 security keys from Yubico last year, as they looked cool and I figured I could have some use for them.
Passwordless is a feature that allows end-users to eschew plain old passwords and move to a more secure posture using any of the modern authentication models that Windows 10 now supports: fingerprint, face recognition, PIN, picture password, and security key. This way, the thinking goes, I wouldn’t have to type in my password – ever again! – but simply use any of the methods available. Things become more secure as my account isn’t accessed through a password but through using something more secure – something that I own, beyond just something that I know.
I had a spare Surface Go, so why not try out how one would go about moving to a passwordless future?
Making sure I have what I need
First, to make my environment more secure by going passwordless, I need an Office 365 tenant. That I have, and it has a few domains attached to it – one is jussiroine.com that I’ll plan on using.
Second, I need Azure Active Directory Premium. This is a per-user license, and I had one spare Enterprise Mobility + Security E5 license. It’s not the cheapest license, and while passwordless doesn’t specifically require this license, Azure Active Directory Premium is required if I want to have my Surface Go devices configured as Azure AD joined.
Third, I need a compatible FIDO2 security key, which I already had – a Security Key by Yubico (Yubikey).
Fourth, I need a test user account. Something that isn’t a Global Admin so that I can replicate the end-user perspective. I provisioned a new account named Joe Bloggs. I attached my EMS E5 license for this account also.
Configuring Azure AD to support passwordless sign-in
As I now had Microsoft Intune license I could use, I started by configuring Intune to Use security keys for sign-in under Azure Portal > Intune > Device enrollment > Windows enrollment > Windows Hello for Business > Properties:
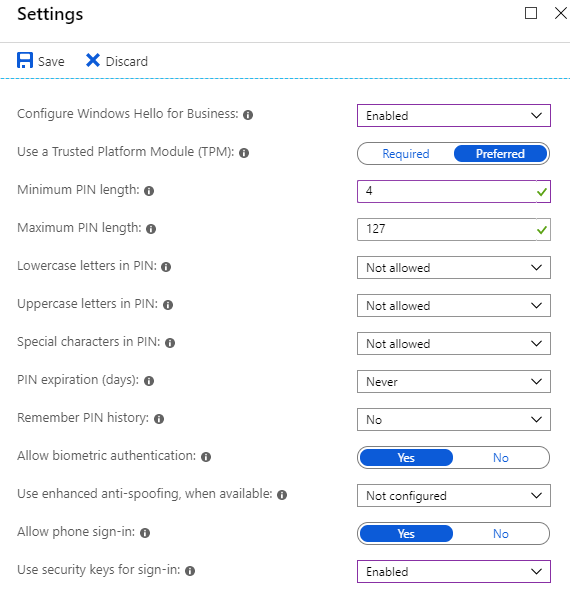
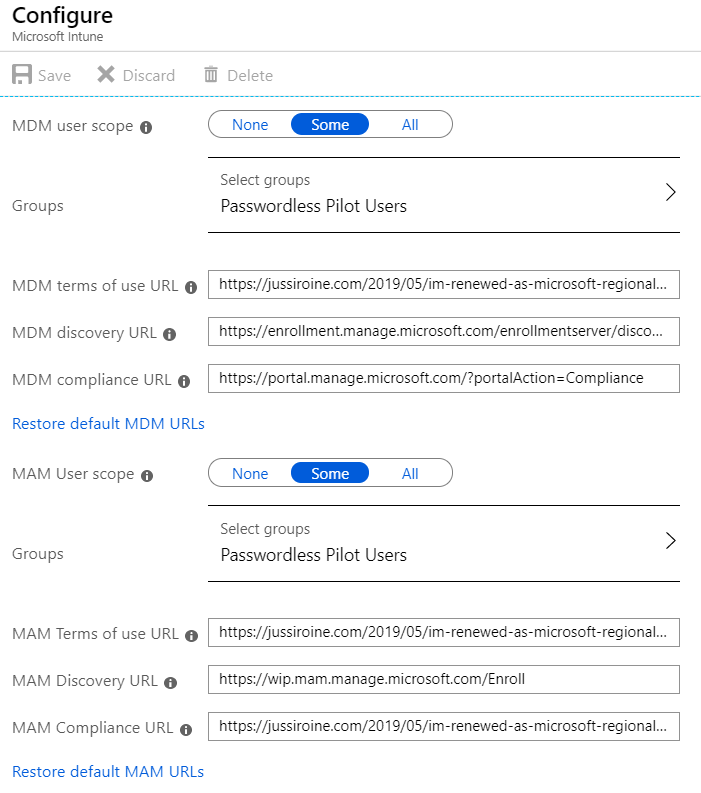
I wanted to verify my Intune settings as it has been a while since I last played around with it in this tenant. Under Azure Portal > Intune > Device enrollment – Windows enrollment, I verified my settings. I realized that with these settings, I needed to add a pilot group to be enrolled, so I quickly provisioned a new security group named Passwordless Pilot Users and added my test account as a member. This security group I also selected for both MDM and MAM user scopes.
I also enabled two preview features for all users in my tenant under Azure Portal > Azure AD > User Settings > User Feature Previews:
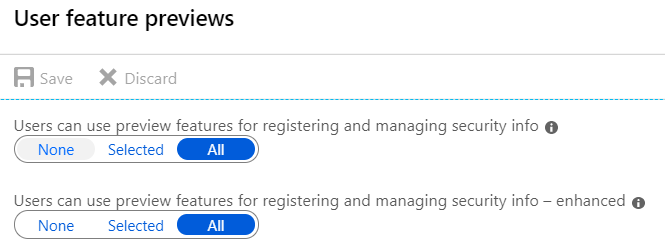
I could have enabled these for specific groups, but as my tenant is only used by myself, I figured this would make things easier in the future.
Finally, to complete passwordless configuration for Azure AD, I enabled authentication settings under Azure Portal > Azure AD > Authentication Methods and verified that the FIDO2 settings looked reasonable for my tests:
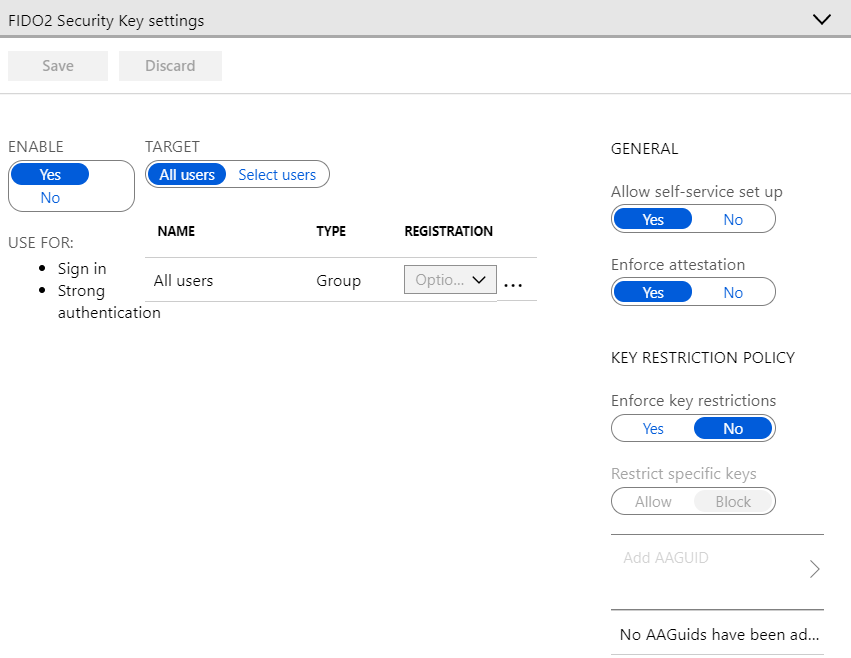
And that’s all that is required in Azure to enable passwordless sign-ins!
Configuring Surface Go for passwordless sign-in
My Surface Go wasn’t joined to Azure AD or a local Active Directory, so it was relatively easy to enroll it to become Azure AD Joined. This way, the device would also be enrolled in Intune.
On the device, under Windows Settings > Accounts > Access work and school, I clicked Connect and then selected Join this device to Azure Active Directory:
I logged in as Joe Bloggs and typed in the password.
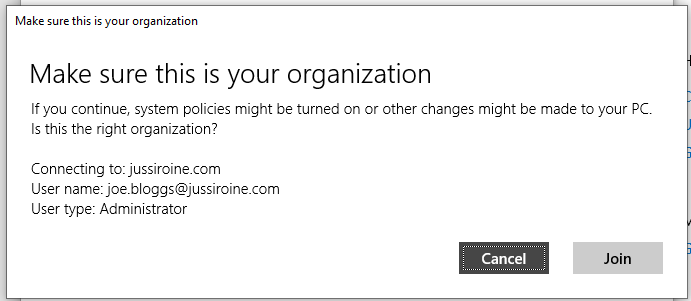
Azure AD wants to make sure I understand what I’m doing, so I need to confirm the enrollment:
And that’s it! My Surface Go is now Azure AD Joined, and Intune managed:
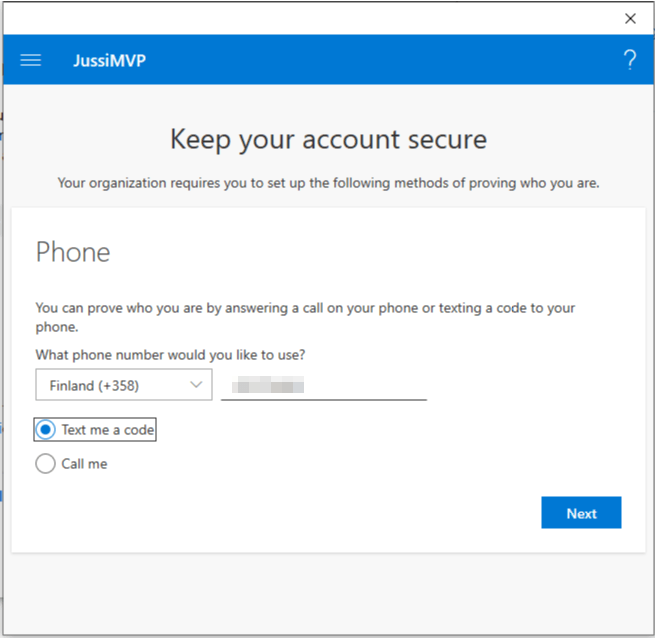
I also needed to verify my security information and set a PIN for Windows Hello for Business:
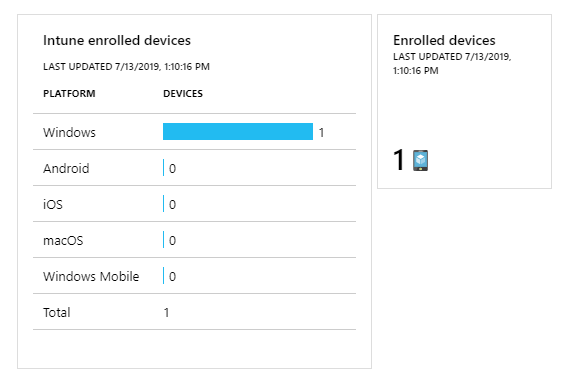
I wanted to verify that my device was, in fact, enrolled in Intune. Checking for active devices in Azure Portal > Intune > Devices I can verify that my Surface Go is managed:
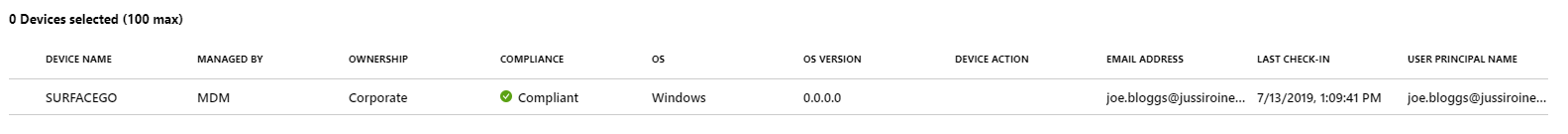
The device shows as compliant. But I haven’t done anything to enable passwordless on the device yet, so let’s complete this one final step next!
Enabling passwordless sign-in for the user
Using my Joe Bloggs account, I open https://myprofile.microsoft.com and select Security Info:
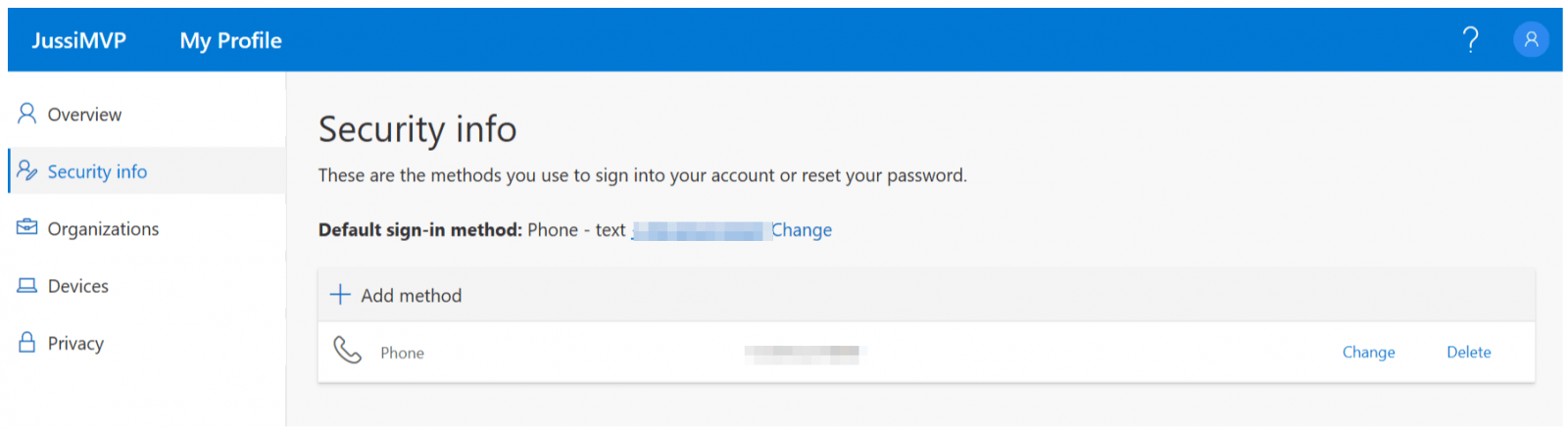
I already have phone-based sign-in enabled. By clicking Add method, I can now add a FIDO2 security key for this user account:
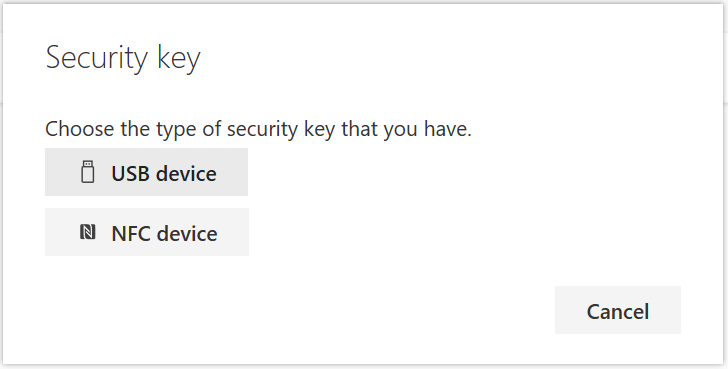
I have the option to choose between USB and NFC enabled devices. I recall reading that Surface Go has built-in NFC support but to avoid any extra issues, I enabled support for USB security keys.
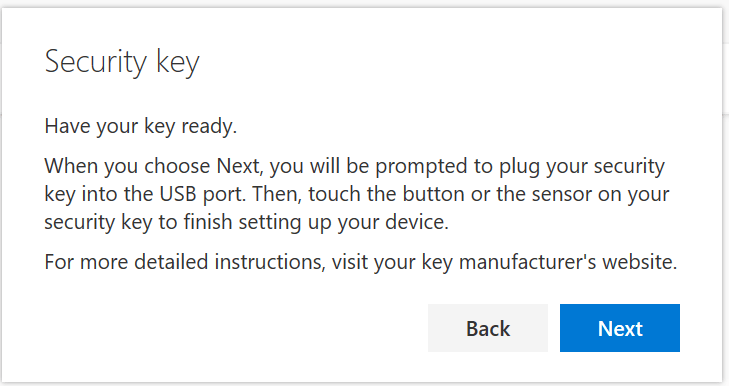
Next, I need to insert the key to my Surface Go:
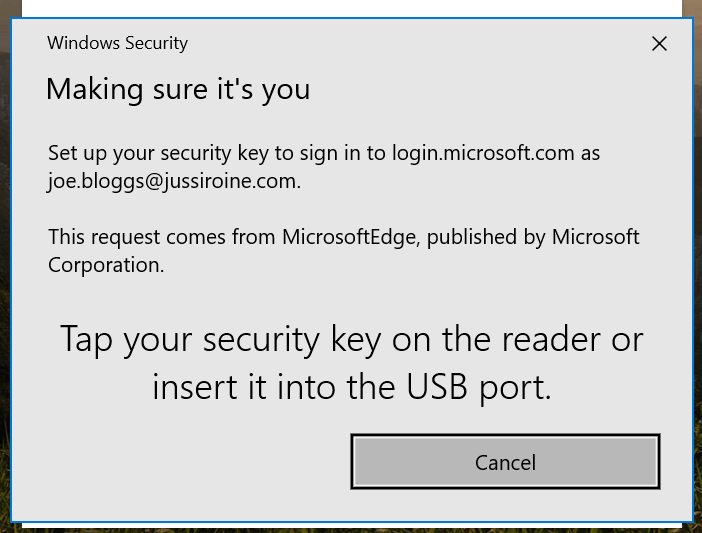
I now need to tap the key to verify I’m present – should I have multiple keys I can make a distinction to which key I want to bind to my account.
Next, I needed to set a PIN to secure the key:
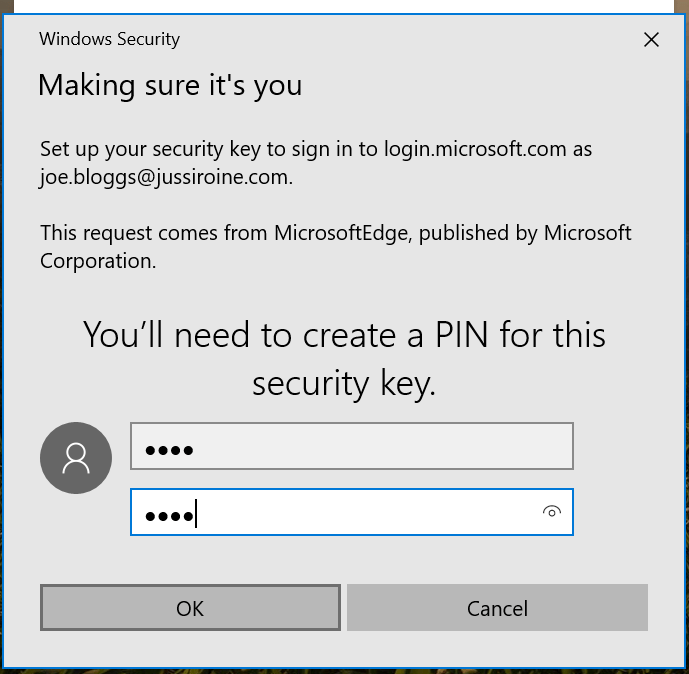
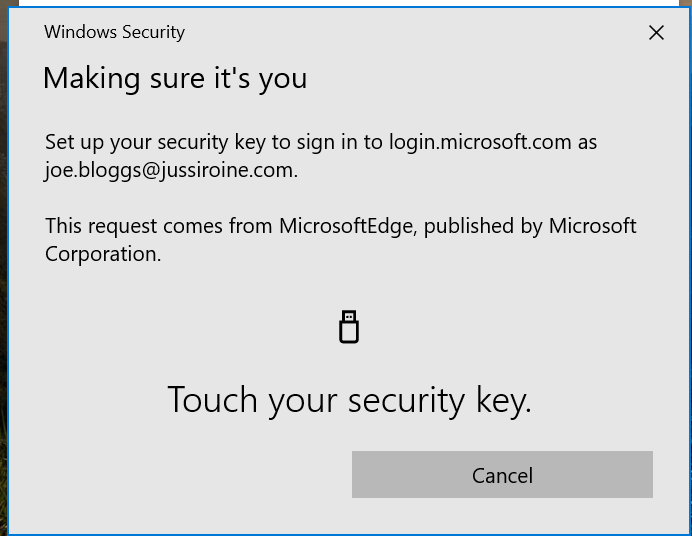
One final confirmation that I still have the key:
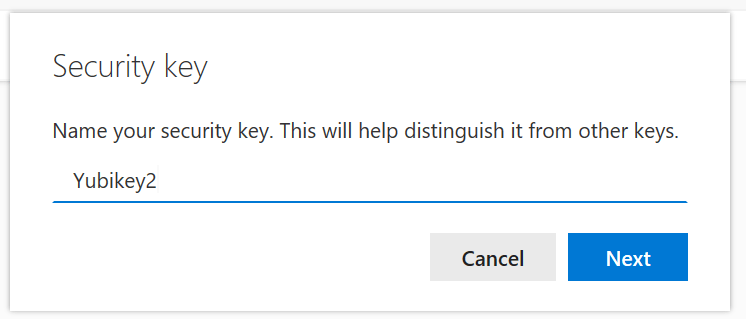
And I’m done! I also get to name the key, should I have multiple keys as they all look the same:
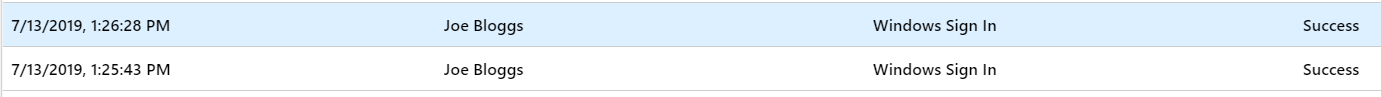
I immediately locked my Surface Go and tried unlocking it with the Yubikey – and it worked!
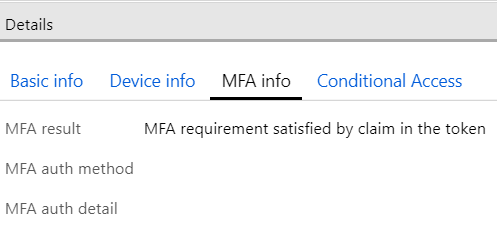
Looking from Azure AD, I can see that authentication was successful:
In summary
Passwordless sign-in using FIDO2 keys is easy to enable, even now when it’s in preview. For the user, it’s relatively easy but does require training and guidance on how to use and manage the key.
This feature also works for browser-based single sign-on, which I tested for https://portal.office.com using Microsoft Edge (the old one, not the new Chromium-based) and Firefox. Support for other browsers is not yet there but hopefully, someday the new Edge and Chrome are also supported.